About “tSpyChecker”
tSpyChecker gives help to detecting spyware.
- Recommended OS
- Android 1.6 or later
- Price
- FREE
- Version 1.7
- Fixed crash on Detect hot apps.
Add the function to permission index list.
Summary
Android smart-phones have different security policy from the conventional cell-phones.
Conventional cell-phones are secured by carrier and hardware maker.
But in android phones, users can install apps freely, and can customize it.
To keep security of android phones, users have to be very careful.
As you know, the app exchanges contact information can get the phone number.
If the app is malicious,
the phone number may be collected by criminals.
To avoid such risks, android shows list of functions that the app uses.
And ask user whether install the app or not.
However, messages android shows are not easy to understand. Almost users install apps without understanding the messages.
In addition, some developers occasionally release their apps with needless authority. That is a fact both developers and user are low of consideration to security.
As the android spreads, it seems that the problem grows big. This is the reason why we released this app. we would like to cause a stir in current situation.
tSpyChecker classifies of apps in your device into safety and dangerous.
When you launch "tSpyChecker", you will be surprised that much apps are classified dangerous.
The apps judged dangerous are not always malicious.
tSpyChecker gives you just a guidance.
Function
Application List
- Displaying a list of all apps installed.
- Displaying dangerous authority as pink icon.
- Updating a application list when you install, update, and uninstall application.
- Excluding app from a application list(It means you trust the app is safty).
- Uninstall the application
- View change("Except an preinstalled apps" or "Only preinstalled apps").
- Launch the application.
- Open Google Play Store.
- Open application manager.
Application Analysis
- Analyzing all function of the app, and explaining the risk simply.
- (Transition to the browser application)Search on the Web by the application name.
Details of the authority
- Extract to dangerous authority of the application, explain more clearly.
- Displaying a description all of the authority of the app.
Application Permission List
- Displaying a list of all permission that application uses.
- Displyaing detailed discription of permission.
Specify permissions to detect
- Specify Communication method to detect
- Specify Permission group to detect
Detect hot apps
- Detect CarrierIQ apps.
- Detect AirPush apps.
- Detect the Movie apps.
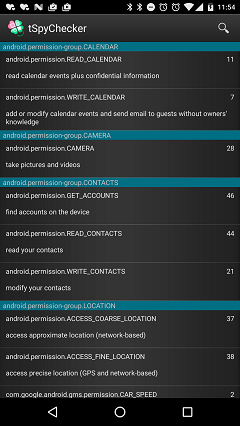
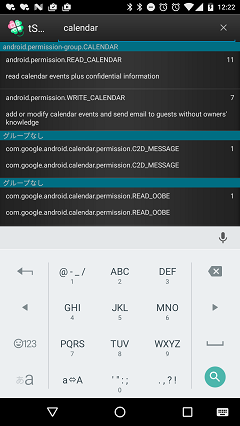
Permission index list
- Display index of the Permissions.
- Add feature to search with the permissions name.
Application List
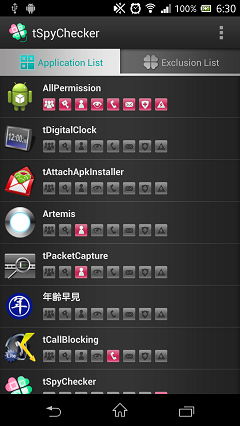
Summary of Application List
Application List displays a list of all installation apps.
When the analyzing finished, the list of applications is shown.
If there are dangerous functions such as information leakage, pink icon is displayed.
You can find dangerous apps with this screen easily.
The risk that each icon means is as follows:
*In the case of malicious apps, It is risky.
For example, you do not need the ability to read the phone book to the general application of wallpaper.You must distinguish that it is really dangerous apps.
The detailed commentary is here.
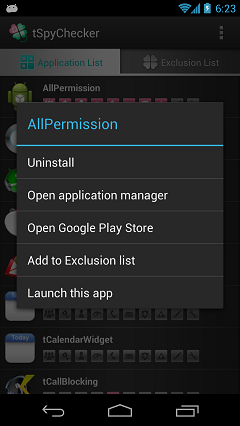
Long-press menu
When press and hold the list, it displays follows menu:
(The displayed menu is different by the application.)
- Uninstall the application
- Open Google Play Store
- Open application manager
- Excluding app from a application list(It means you trust the app is safty)
- Launch the application
Exclusion List
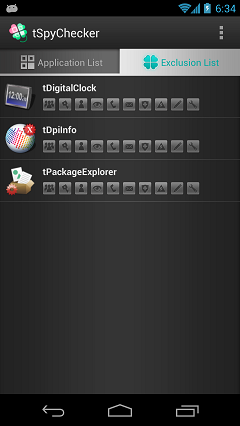
Summary of Exclusion List
Exclusion List is displayed a list of apps that excluded.
Tap "Exclusion List" of the right tab of the "Application List".
If you judge the app is safe, you can exclude it from Application List.
The "Exclusion List" screen lists the excluded apps.
Long-press menu
When press and hold the list, it displays a "Restore to App list" and "Uninstall" menu.
Application Analysis
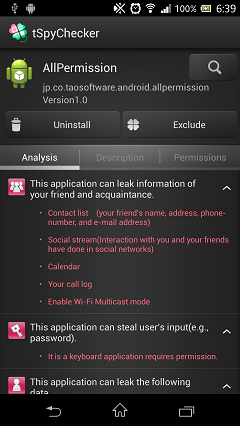
Summary of Application Analysis
This screen detects dangerous authority of the apps, and display a result.
When swipe a Application List or Exclusion List, this screen will be shown.
This screen shows detected risks of the app with description that is easy to understand.
Please confirm whether there functions are really required or not.
For example, if the wall paper app has a function of the acquisition
with a phone number and a function to send a short email, It seems dangerous.
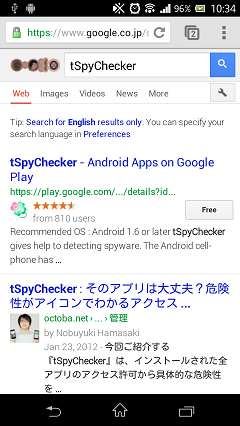
In addition, the web search by the application name, when you click the search button.(Transition to the browser application)
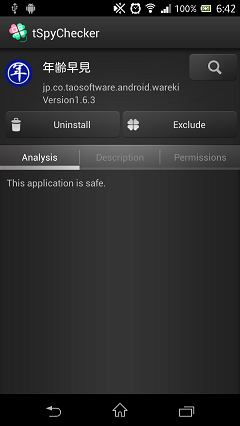
When there are no dangerous authority
This screen is displayed when the application doesn't have any dangerous authorities.
"Uninstall" button
When tap a "Uninstall" button, you can uninstall the app.
"Exclude" button
When tap "Exclude" button, you can exclude the app from the list.
Application Description
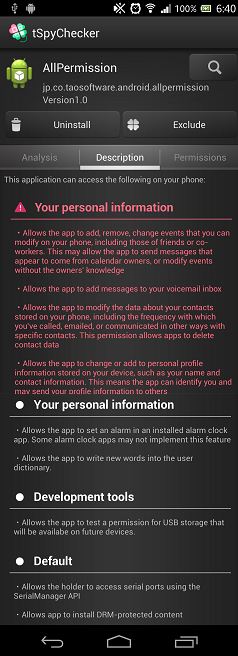
This screen shows a description all of the authority of the app.
Swipe to "Description" screen, detailed description of the app is shown.
You can see a detailed description of application functionality.
Please scroll the screen to see long descriptions.
This screen displays the explanation that is more detailed than Android Settings.(Settings>Applications>Manage applications)
Orange color explanation means the protection level of authority is "dangerous".
The app can access the user's private data of high-risk features.
White color explanation means a protection level of authority is "normal", describes the low-risk features.
Application Permissions
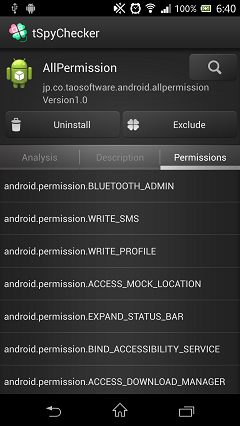
It is a screen for the developers who can confirm permissions with a cord.
Swipe to "Permissions" screen, Application permission screen is displayed.
All of authorities admitted for application are listed.
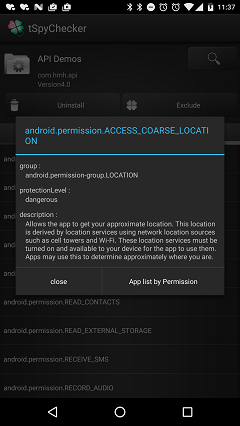
Show a detailed description, group, and protection Level of authority when you tap the list.
Setting
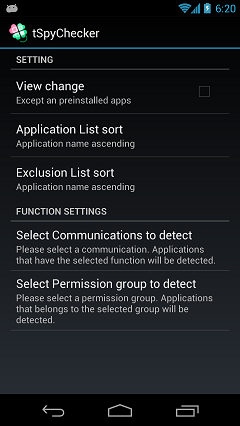
tSpyChecker features the following settings.
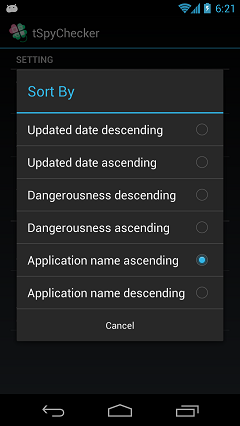
List sort setting
You can be changed to a display "Except an preinstalled apps" or "Only preinstalled apps".
Also, You can change the order of the list by tapping "Updated date descending", "Application name ascending", "Dangerousness descending", etc.
"Dangerousness descending" is the total number of dangerously Permission.
It is not in descending order of total number of pink-icon.
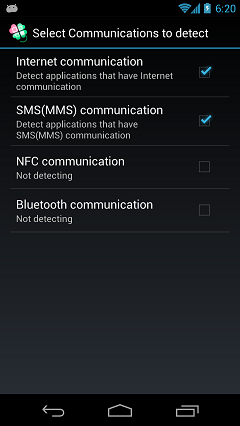
Select Communications to detect
You can change detection of communication method from "Internet communication", "SMS communication", "NFC communication" and "Bluetooth communication".
By default, "Internet communication" and "SMS communication" have been checked.
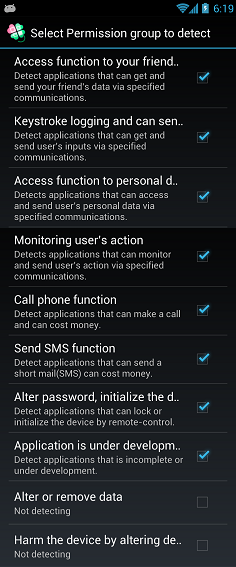
Select Permission group to detect
You can change detection of dangerous Permission group.
Applications that belongs to the selected group will be detected.
"Keystroke logging and can send it","Access function to personal data and can send it" and "Monitoring user's action"
is detected in combination with external communication tools that is checked in your settings.
By default, permission that should be aware have been checked.
For additional information, please visit at next chapter.
A commentary of dangerous authority
This chapter describes the results found by the tSpyChecker.
Leakage of your friends information
| Authority icon | Commentary |
|---|---|
| When application have permission of access your friend and family information and communication tools that is checked in your settings, display the icon. Because the application can access and send friends data via specified communications, this is risky. For example, When application have "android.permission.READ_CONTACTS" and "android.permission.INTERNET", Allows an application to leak the friends name, address, and phone number. |
Keystroke logging and send
| Authority icon | Commentary |
|---|---|
| When application have "android.permission.BIND_INPUT_METHOD" and communication tools that is checked in your settings, display the icon. Allows the holder to bind to the top-level interface of an input method. Because the author of this application can steal user's input(e.g., password) illegally without permission, using communication tools that is checked in your settings, this is risky. |
Leakage of personal information
| Authority icon | Commentary |
|---|---|
| When application have permission of access personal information and communication tools that is checked in your settings, display the icon. Because the application can access and send user's personal data via specified communications, this is risky. For example, When application have "android.permission.READ_CONTACTS" and "android.permission.INTERNET", Allows an application to leak the user's contacts data. |
Combination as follows:
| Communication | Authority of acquire personal information |
|---|---|
| Selected communication tools Setting is here |
GET_ACCOUNTS |
| USE_CREDENTIALS | |
| READ_SMS | |
| RECEIVE_SMS | |
| RECEIVE_MMS | |
| RECEIVE_WAP_PUSH | |
| READ_CONTACTS | |
| READ_CALENDAR | |
| READ_USER_DICTIONARY | |
| READ_PROFILE | |
| READ_LOGS | |
| READ_PHONE_STATE |
Monitoring user's action
| Authority icon | Commentary |
|---|---|
| When application have permission of access to user's action and communication tools that is checked in your settings, display the icon. Because the application can monitor user's action via specified communications, this is risky. For example, When application have "android.permission.ACCESS_FINE_LOCATION" and "android.permission.INTERNET", Allows an application sent outside of your whereabouts at all times. |
Combination as follows:
| 外部通信権限 | 行動監視権限 |
|---|---|
| Selected communication tools Setting is here |
RECORD_AUDIO |
| RECORD_AUDIO, PROCESS_OUTGOING_CALLS | |
| CAMERA | |
| ACCESS_FINE_LOCATION | |
| ACCESS_COARSE_LOCATION | |
| RECEIVE_SMS | |
| RECEIVE_MMS | |
| RECEIVE_WAP_PUSH | |
| ACCESS_WIFI_STATE | |
| com.android.browser.permission.READ_HISTORY_BOOKMARKS | |
| READ_LOGS | |
| GET_TASKS | |
| BATTERY_STATS |
Call phone function
| Authority icon | Commentary |
|---|---|
| When applications have "android.permission.CALL_PHONE" or "android.permission.PROCESS_OUTGOING_CALLS", display the icon. Allows the applications can make a call without the permission of the user. Malicious applications may cause unexpected calls on your phone bill. This is risky to cost a rate and leaking a phone number. And, the application that have "android.permission.CALL_PHONE" and "android.permission.PROCESS_OUTGOING_CALLS" be dangerous because it can be transferred to a different phone number. |
Send SMS function
| Authority icon | Commentary |
|---|---|
| When application have "android.permission.SEND_SMS", display the icon. Malicious applications may cost you money by sending messages without your firmation. |
Alter password, initialize the device
| Authority icon | Commentary |
|---|---|
| When application have "android.permission.BIND_DEVICE_ADMIN", display the icon. Allows the holder to send intents to a device administrator. Should never be needed for nomal application, it is risky. |
Application is under development
| Authority icon | Commentary |
|---|---|
| When application have authority group "DEVELOPMENT_TOOLS", display the icon. Should nevere be needed for nomal application, it is risky. In addition, signing in Debug Mode, is also displayed in the debug-enabled application. |
Permission as follows:
| Authority |
|---|
| CHANGE_CONFIGURATION |
| DUMP |
| SET_DEBUG_APP |
| SET_PROCESS_LIMIT |
| SET_ALWAYS_FINISH |
| SIGNAL_PERSISTENT_PROCESSES |
| WRITE_SECURE_SETTINGS |
Alter or remove data
| Authority icon | Commentary |
|---|---|
| When application have authority that can falsify data, display the icon. For example, When application have "android.permission.WRITE_CONTACTS", Allows an application to modify and delete the contect(address) data stored on your phone, it is risky. |
Permission as follows:
| Authority |
|---|
| WRITE_CALL_LOG |
| WRITE_SOCIAL_STREAM |
| WRITE_SMS |
| WRITE_CONTACTS |
| WRITE_CALENDAR |
| WRITE_USER_DICTIONARY |
| com.android.browser.permission. WRITE_HISTORY_BOOKMARKS |
| WRITE_EXTERNAL_STORAGE |
| MOUNT_FORMAT_FILESYSTEMS |
| WRITE_PROFILE |
| RECEIVE_SMS |
| RECEIVE_MMS |
| RECEIVE_WAP_PUSH |
| USE_CREDENTIALS |
Harm the device by altering device's settings
| Authority icon | Commentary |
|---|---|
| When application have authority to destabilize the operation of the terminal, display the icon.
For example, When application have "android.permission.WAKE_LOCK", Allows and application to prevent the phone from going to sleep, Because of increase in battery consumption, it is risky. |
Permission as follows:
| Authority |
|---|
| CHANGE_CONFIGURATION |
| CHANGE_NETWORK_STATE |
| CHANGE_WIFI_MULTICAST_STATE |
| CHANGE_WIFI_STATE |
| WRITE_APN_SETTINGS(Android4.0) |
| WRITE_SETTINGS |
| WRITE_SYNC_SETTINGS |
| SET_TIME_ZONE |
| MOUNT_UNMOUNT_FILESYSTEMS |
| KILL_BACKGROUND_PROCESSES |
| REORDER_TASKS |
| SYSTEM_ALERT_WINDOW |
| DISABLE_KEYGUARD |
| WAKE_LOCK |
Detect hot apps
tSpyChecker detects the applications and application modules that have became a topic on the Internet.
Even if the developer says "no problem", many users have seen the app as a problem, tSpyChecker will detects the app.
It's dangerous to continue using the app that have been recognized to problems by the application developer itself.
Even if the developer say to "no problem", this apps detects the software.
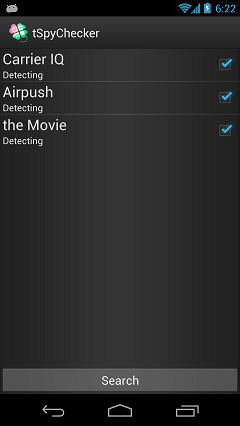
Screen of selecting detect app
Display a screen of selecting detect app when you tap "Detect Hot Apps" on menu.
Then check the app discovery. And check the box against the application you want to discover.
Display a detailed explanation when you tap the list.

Screen of Detected Result
This appears only type that was detected.
If not found will not be displayed.
Display a detailed explanation when you tap the list.
Carrier IQ
Carrier IQ was discovered in December 2011.
It has been a problem as software which records a user's operation without a user's permission by the mobile phone maker and a carrier.
Although it aimed at using for the improved quality of a product by using the trend data collection of the mobile phone, user was not told that data collection.
Even if Carrier IQ is installed, sometimes data collection is not carried out or sometimes only the wreckage of Carrier IQ is installed, it is various.
In order to uninstall Carrrier IQ, root privilege is needed so uninstallation is usually impossible.
Please refer to the following for detailed information.
To uninstall Carrier IQ, you need to get a root.
So usually, you can not uninstall the app Carrrier IQ.
For additional information, please visit the following:
- Searching'What is Carrier IQ'
- Carrier IQ, Inc.
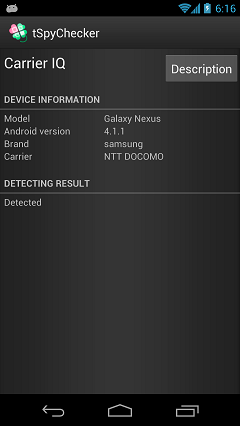
Detect Carrier IQ
Screen of detected Carrier IQ.
Display a detailed explanation about Carrier IQ when you tap the "Description" button.
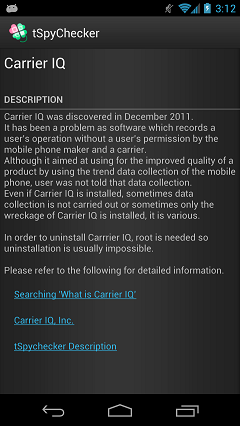
Description screen of Carrier IQ
Detailed description screen of Carrier IQ
Detection Logic of Carrier IQ
This application has been created with reference to FORTINET "Carrier IQ on Android FAQ".
When the following files exist, Reports that "Detected".
This app does not determine that is actually running Carrier IQ.
- /system/app/com.htc.android.iqagent.apk
- /system/app/com.carrieriq.tmobile.apk
- /system/app/com.carrieriq.iqagent.apk
- /system/app/com.carrieriq.attrom.apk
- /system/app/HtcLoggers.apk
- /system/app/HTCIQAgent.apk
- /system/bin/iqfd
- /system/bin/iqd
- /system/bin/iqmsd
- /system/lib/libciq_client.so
- /system/lib/libciq_htc.so
- /system/lib/libhtciqagent.so
- /system/lib/libiq_service.so
- /system/lib/libiq_client.so
- /system/etc/iqprofile.pro
There may be to be addressed other than the above in the future, in which case please contact us.
AirPush
Airpush is the application module for ads provided by Airpush Inc.
Ads is displayed on notification bar of devices instead of application's display area.
Even if it does not use an application, ads is displayed and a user does not know which application displayed ads.
Please use this function when ads displayed on a status bar and you don't know how to delete it.
For additional information, please visit the following:
- Searching 'What is AirPush'
- AirPush.com
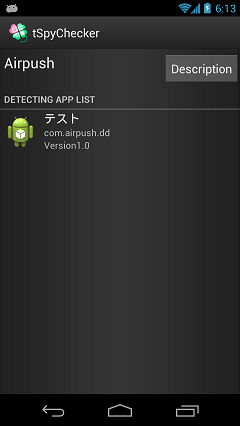
Detect AirPush
Screen when AirPush detected
Displays all of the applications using AirPush.
The ads will be deleted from notification bar when all applications are deleted from the list.(Even one application remains, the ads keep displaying.)
Detection Logic of AirPush
AirPush.com expresses that the AirPush advertisement delivery system is no problem.
Thus, AirPush ad module is being used openly. Perhaps It is not included in applications secretly.
Therefore, tSpyChaecker reports "Detected" when the following symbols have been found in AndroidManifest files.
- com.airpush.
- com.Leadbolt.
- com.appenda.
- com.iac.notification.
- com.hairstyles.teens
- com.funnypranks
- com.enlightenedapps.androidnewtworksignalbooster
- com.antonio.thermo2.activity
- org.tonee.cuteanimals
- com.antonio.fruits.free
- com.killu.mhl
- com.mrgorsky.horrorsounds
- jqsoft.apps.mysettings
It seems addtional logic will be needed in the future. If you find other symbols should be detected, please let us know.
the Movie
The Movie is a malware that was discovered in April 2012.
Many applications has been released as the Movie.
Their application name was named 'the Movie' adding after the famous keyword.
It is said that the number of installations are more than hundred thousand.
Although the application provides the function of to download videos, it will send names and phone numbers in contacts to the server at the same time.
At present these apps has been removed from Google Play, and the author's account removed too.
The server used to receive data from the Movie has been stopped, so if you installed the Movie application, it doesn\'t send info in contacts.
However, who have installed these apps before the server was stopped, phone book data could have been already extracted.
Please refer to the following for detailed information.
Symantic blog:
"The Movie" Malware Steals Personal Information from Japanese Android Users
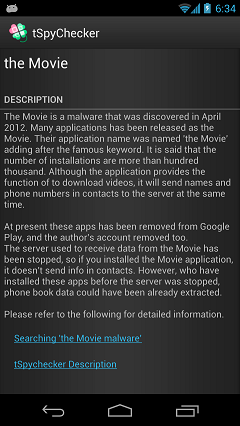
Description screen of the Movie
Detection Logic of the Movie
tSpyChecker will search applications that are given package name below.
- jp.iketerudouga
- jp.subarasikidouga
- jp.douzinviewer
- jp.setunaigirl
- jp.yutorinohutomomo
- jp.eroperiax
- jp.poruchiokupaa
- jp.hhhdougakan
- jp.kabukichogozennizi
- jp.animedouga
- jp.gurabiadouga
- jp.himatubusidouga
- jp.nakerudouga
- jp.nikonikodougamatome
- jp.oomosirodougamatome
- jp.youtubedougamatome
- jp.youtuubedougamatome
- jp.yuutubedougamatome
- jp.bizindouga
- jp.geinoudouga
- jp.kowaidouga
- jp.waraerudouga
- jp.youtubebedouga
- jp.yoututubebedouga
- jp.yoyotubedouga
Permission index list
Download and Install
Download from Google Play
Google Play tSpyChecker(Closed)
Release Note
- Version 1.0.0
- First release
- Version 1.0.3
- Bug fix.
- Version 1.1
- Support for Android4.0
Detects applications that can monitor and send user's action(e.g., whereabouts) via specified communications.
Detects applications that can access and send user's personal data(e.g., accounts data) via specified communications.
Detect applications that is incomplete or under development.
Detect applications that can lock or initialize the device by rem
ote-control.
Detect applications that can alter or remove data.
Detect applications that can harm the device by altering device's settings.
Add Setting menu "Select Permission group to detect"
Add Setting menu "Select Communications to detect"
tSpyChecker can be moved to SD card - Version 1.2
- Detect hot apps.(CarrierIQ)
- Version 1.3
- Detect hot apps.(the Movie)
- Version 1.4
- Detect hot apps.(AirPush)
Add setting menu "View change".("Except an preinstalled apps" or "Only preinstalled apps")
Add "Launch this app" to long-press menu on Application List.
Add "Open Google Play Store" to long-press menu on Application List.
Add "Open application manager" to long-press menu on Application List. - Version 1.5
- Detects applications that can access and send friend data(e.g., Friend's name, contacts, address) via specified communications.
For additional information, please visit at here.
Support for Android 4.1 and 4.2
Navigate by swiping the screen at the top screen and details screen.
Add a link to the Privacy Policy to "About" screen
Add a "Help" screen
Change the overall design
Privacy Policy
Privacy Policy (Japanese).
Precautions for Software
You expressly acknowledge and agree that use of the Software is at your sole risk. The Software and related documentation are provided "AS IS" and without warranty of any kind and Taosoftware EXPRESSLY DISCLAIMS ALL WARRANTIES, EXPRESS AND IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE. TAO SOFTWARE DOES NOT WARRANT THAT THE FUNCTIONS CONTAINED IN THE SOFTWARE WILL MEET YOUR REQUIREMENTS, OR THAT THE OPERATION OF THE SOFTWARE WILL BE UNINTERRUPTED OR ERROR-FREE, OR THAT DEFECTS IN THE SOFTWARE WILL BE CORRECTED. THE ENTIRE RISK AS TO THE RESULTS AND PERFORMANCE OF THE SOFTWARE IS ASSUMED BY YOU. FURTHERMORE, TAO SOFTWARE DOES NOT WARRANT OR MAKE ANY REPRESENTATIONS REGARDING THE USE OR THE RESULTS OF THE USE OF THE SOFTWARE OR RELATED DOCUMENTATION IN TERMS OF THEIR CORRECTNESS, ACCURACY, RELIABILITY, CURRENTNESS, OR OTHERWISE. NO ORAL OR WRITTEN INFORMATION OR ADVICE GIVEN BY TAO SOFTWARE OR TAO SOFTWARE'S AUTHORIZED REPRESENTATIVE SHALL CREATE A WARRANTY OR IN ANY WAY INCREASE THE SCOPE OF THIS WARRANTY. SHOULD THE SOFTWARE PROVE DEFECTIVE, YOU (AND NOT TAO SOFTWARE OR TAO SOFTWARE'S AUTHORIZED REPRESENTATIVE) ASSUME THE ENTIRE COST OF ALL NECESSARY SERVICING, REPAIR OR CORRECTION.
UNDER NO CIRCUMSTANCES INCLUDING NEGLIGENCE, SHALL TAO SOFTWARE, OR ITS DIRECTORS, OFFICERS, EMPLOYEES OR AGENTS, BE LIABLE TO YOU FOR ANY INCIDENTAL, INDIRECT, SPECIAL OR CONSEQUENTIAL DAMAGES (INCLUDING DAMAGES FOR LOSS OF BUSINESS PROFITS, BUSINESS INTERRUPTION, LOSS OF BUSINESS INFORMATION, AND THE LIKE) ARISING OUT OF THE USE, MISUSE OR INABILITY TO USE THE SOFTWARE OR RELATED DOCUMENTATION, BREACH OR DEFAULT, INCLUDING THOSE ARISING FROM INFRINGEMENT OR ALLEGED INFRINGEMENT OF ANY PATENT, TRADEMARK, COPYRIGHT OR OTHER INTELLECTUAL PROPERTY RIGHT, BY TAO SOFTWARE, EVEN IF TAO SOFTWARE OR TAO SOFTWARE'S AUTHORIZED REPRESENTATIVE HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES.
Addition
We make a customized development of software for Android and iPhone. Please feel free to contact us at any time.